Michaela Zhirova and Marjo Koivisto
Introduction
Cyber attacks have almost doubled in past five years, and come with an estimated price of USD90 trillion according to the World Economic Forum.(1) Indeed, the pace and scale at which new technologies are being introduced across industries is expanding the cyber attack surface malicious actors can exploit. This will only
increase as the trials and pilots for 5G accelerate. Cyber attacks on both companies and governments include, but are not limited to, infringement of privacy and confidentiality, expensive theft of data, compromise of system integrity and accessibility, and destruction of data. In addition, despite cyber attacks becoming both more frequent and more sophisticated at an alarming pace, companies seem to under-invest in cyber risk management. In fact, one of the two main challenges Chief Information Security Officers identify is a lack of resources.This Responsible Investments white paper outlines why we see cyber security as an increasingly materializing ESG risk factor across sectors, and speculates about the key financial implications of cyber incidents we have identified for corporates. Further, we have scored cyber threat exposure across industries and provide our view of those at high risk. As part of our ESG engagement practice, we have developed a view to incorporate best practices in cyber threat identification, governance, contextual awareness and implementation of cyber security measures. We advocate a questionnaire to assist in establishing a benchmark of cyber resilience of businesses, and outline our expectations of best practices for companies to express cyber security preparedness.

Digital cybersecurity and network protection concept.
Major cyber attacks: some lessons learnt about financial implications for business
Because cyber attack identification, evaluation and elimination can take a long time and result in operational loss,the cost to companies continues to edge higher. This is evidenced in some of the largest ransomware attacks of all time, e.g. NotPetya. The NotPetya ransomware attack spread from Ukrainian servers in 2017 to large global businesses resulting in losses totaling over USD10 billion(2) in damage to companies and affecting computers around the world. It infected companies in multiple industries, from medical service providers to a major logistics company (A.P. Møller-Maersk), bringing down its operations for more than 10 days. (3)
Marriott is another large-scale company that has been subjected to a significant ransomware attack. On September 8, 2018, an internal security tool flagged a suspicious attempt to access the internal guest reservation database for Marriott’s Starwood brands. This prompted an internal investigation that determined that the Starwood network, which was acquired by Marriott in 2016, had been compromised sometime in 2014. According to reports, at the time of the attack, the former Starwood hotels had not been migrated to Marriott’s own reservation system and were still using IT infrastructure inherited from Starwood. In their investigation, Marriott found data that the attackers had encrypted and attempted (probably successfully) to remove personal data from the Starwood systems. Marriott managed to decrypt the data and discovered that it included information from up to 500 million guest records, many included extremely sensitive information like credit cards and passport numbers.
The financial implications of the ransomware incident on Marriott were severe. In July 2019, they were fined USD126 million from the UK due to General Data Protection Regulations (GDPR). Their Q2 2019 earnings reported a 65% drop in profit down to USD232 billion or 69 cents per share.(4) The hotel chain was also fined 1.5 million Lira (~$265,000) by the Turkish data protection authority (not under the GDPR legislation) for the incident, highlighting how one breach can result in multiple fines globally. Finally, in March 2019, there was a USD28 million fine (which impacted the company’s bottom line by only USD3 million because Marriott had cyber insurance).
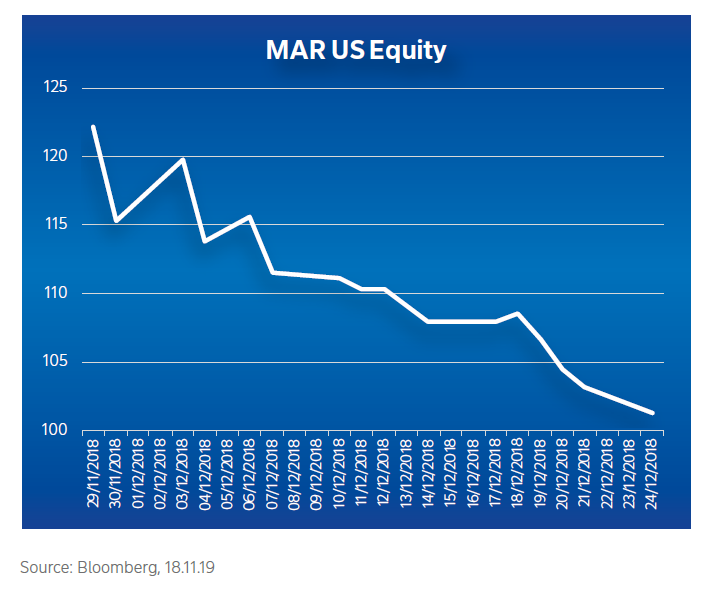
The breach to Marriott became public on 30 November 2018. In the month following the news, Marriott’s share
price plunged by 17%, albeit in the context of an otherwise volatile December and high performance the previous
year.(5)
‘ Because cyber attack identification, evaluation and elimination can take a long time and result in operational loss, the cost to companies continues to edge higher. ‘
Empirical analyses of the market show investors indeed punish companies with data leaks. This should be a strong motivator for corporates to focus on better cyber security preparations. A recent study of companies listed on the NYSE that experienced a publicly reported breach of 1 million or more records showed that share prices hit a low point approximately two weeks after the news went public, falling 7.27% on average, and underperforming the NASDAQ by -4.18%.(6) The same study found that even if the effect of the breach on the share price diminished over time, these companies’ share prices underperformed the market (on a 1 or 2 year time interval).
Cyber risk to value creation: efforts at estimation of cost and revenue impact
Given that predicting individual cyber incidents is anyone’s guess, it is challenging to price cyber risk. Moreover, a Deloitte study recently suggested that insurers are hesitant to underwrite cyber risk because of the challenges of financial modelling of a moving target as new threat actors and types of attack emerge regularly.(7) That said, high profile cyber- attacks have also resulted in more sophisticated underwriting, and indeed cyber insurance providers indicate that over the past 3-4 years, scenario-based modelling inputs have become increasingly uniform across the major providers of cyber insurance.(8)
In a 2019 study of G2000 companies, Accenture reported the global average cost of a cybercrime attack per company in 2017 was USD11.7 million, but the average cost, alongside the number of breaches, had increased by USD1.3 million on a y/y basis.(9) For small/mid cap companies, with fewer resources dedicated to IT and operational cyber resilience, the cost could be even higher. Yet there is limited disclosure of costs of incidents, or for the uniqueness of costs per incident, e.g. downtime or required cyber security spending. Hence, in this paper, we do not attempt to estimate costs. Instead, we have mapped the sectors in which value creation is most exposed to cyber incidents. We focus on some of the most vulnerable sectors, estimating which part of a company’s business could be most at risk. To avoid getting into technological particularities, our scoring conceptualized risk at a high level. In order to arrive to a sector score, we rated sectors according to three groups of indicators: potential for harm (to property, persons, the environment, or disruption), type of system weakness (lack of awareness, expertise, or communication), and exposure (sensitive business model, storage of valuable or sensitive data). For the sector ratings in the first and third group of indicators, we analyzed the operating models of the sectors in question in order to identify relevant impacts. A second group of indicators deals with potential weaknesses in practices: preparedness and governance, age of systems, awareness, expertise, and communication. For the rating of this group, we evaluated approximately 30 trade papers, CISO conference papers, and consultant studies to arrive at an understanding of the most common systemic issues in a given sector. An additional dimension of exposure is whether the business model is built on data, or whether the data businesses in the sector tend to store is particularly sensitive or valuable. Put simply, we scored companies on whether they have proper governance of cyber risk, whether their systems are up to date, whether they have access to the necessary know how, and whether the different parts of the organisation speak to each other enough to integrate security solutions effectively.
The most exposed sectors fall roughly into two groups: industrials and manufacturing. Both score medium high for exposure, but get dragged down by the lack of investment in systems and expertise. Systems in the restaurant and leisure sectors tend to significantly lack the sophistication necessary to meet the demands of processing the sensitive customer data they handle.
‘A core concern, expressed by CISOs is that companies are, in general, under spending on cyber incident preparedness.’
Background on our expectations for companies
As it is not possible to be ‘bullet-proof’ against cyber-attacks, companies should aim to be sufficiently prepared to respond to potential cyber breach incidents. One of the core actions should be achieving a clear understanding of which parts of the business model (revenues) are most exposed to material cyber risks. As per the above, an incident could bring down operations for days, resulting immediately in lost contracted revenue. For example,consider the telecommunications industry, which tends to be better prepared than the high-risk cases we site above. A large telecommunications company could have around 20-30% of its total revenue in enterprise service and managed business revenues governed by Service Level Agreements with enterprise customers. This could be enforced by customers in case of breach, making the service provider liable. To take another example, digital companies, whose main product is source code, would not be able to sell their product if the code was breached, resulting in ever larger losses of revenue. Another core concern, expressed by CISOs, is that companies are, in general, underspending on cyber incident preparedness. According to an IBM study,10 companies should ideally spend 14% of their IT budget on cyber security, but if we assess the sectoral averages (eg. 3,73% of their revenues for IT companies) in the context of 2018 revenues, it becomes clear companies are underspending. It is challenging for companies to publicly disclose their cyber security spending budget, but we think investors must ask for details.

What we expect of companies cyber security preparations
As part of our research, we have developed a questionnaire on cyber security preparedness for companies we invest in, with the objective of understanding our cyber risk exposure in those investments. Our questionnaire has 17 questions, focused on identifying, governing, implementing and calculating (material) cyber risk exposure.
We have determined best practices from responses across sectors to our questionnaire, which form four primary expectations related to cyber preparedness:
- Cyber risk identification: A company’s unawareness of the most material cyber risks to its business is a red flag. We expect business risk appetite to be tailored to awareness about the business’ material cyber risks, and we expect to see a cyber asset strategy concretely established. For example, an asset like a source code must be protected in a differentiated way from personal data.
- Governance: Cyber resilience should be a board level issue for companies. Privacy and data policies should have wide application, covering third parties, in which a minimum standard is expressed in order to do business with those third parties. We prefer to see quarterly check in on cyber skills at the board level.
- Context: Best practice is to be aware of the need for a stronger ecosystem on cyber resilience. Best practice for context and ecosystem is knowledge sharing and collaboration on priorities with peers.
- Implementation: Companies with best practice have solid incident anticipation and “damage control” processes in place. We also expect that best practice companies have cyber security integrated at the product level early in product development, and are managing their cyber assets and costs effectively.
Conclusions
The immense business opportunities brought on by digitization can come with a multi-trillion dollar price tag if corporates do not prepare adequately for cyber attacks. The lack of investment in cyber security systems and expertise, the lack the sophistication necessary to meet the demands of processing sensitive customer data, and non-existent incident recovery plans are among the red flags for us in high-risk sectors. In this paper, we referred to market data indicating investors clearly react to cyber incidents and company management of cyber incidents. We reflected on where financial implications of cyber incidents could be seen. Finally, we offered our expectations of best practices of cyber security resilience in conclusion to our analysis.
- World Economic Forum, The Cybersecurity Guide for Leaders in Today’s Digital World, 2019.
- Source: The Untold Story of NotPetya, the Most Devastating Cyberattack in History, 2018 Wired Magazine.
- Maersk was hardly the only company experiencing an IT meltdown at the hands of NotPetya: food and beverage manufacturer Mondelez, pharmaceutical giant Merck, advertising agency WPP, health and hygiene products maker Reckitt Benckiser, French construction company Saint-Gobain and FedEx’s European subsidiary TNT Express were among thousands of multinationals impacted.
- Source: Marriott Takes $126 Million Charge Related to Data Breach, 2019 Wall Street Journal.
- According to analysts, Marriott’s stock was perhaps due for some correction in 2018, having rocketed 64% higher in 2017. However, pressure became more pronounced in the second half of 2018 due to a confluence of factors, and then specifically the cyber breach news.
- Bischoff, Paul, Comparitech: How Data Breaches Affect Stock Market Share Prices, 28 Nov 2019.
- Source: Deloitte, 2018
- The cyber insurance market is estimated to be in the low billions of dollars. Fitch estimates that in 2018, cyber insurance total written premiums grew 8% to USD2 billion. Source: Fitch Ratings 2019,“Cyber Insurance Growth Slows, Market Remains Untested,” May 14, 2019.
- Ponemon Institute LLC and Accenture, The Cost of Cybercrime, 2019.